A Web Application Firewall, often abbreviated as WAF, is a pillar of modern web security. It serves as a protective shield for web applications and websites, relentlessly standing guard against a barrage of online threats and vulnerabilities. In an era when the digital landscape is constantly under siege from malicious actors seeking to exploit weaknesses in web applications, a WAF acts as the first line of defense, intercepting and neutralizing these threats in real-time.
Much like a vigilant sentry, a WAF scrutinizes all incoming and outgoing web traffic, inspecting the data with precision and diligence. Its primary mission is to identify and thwart a wide range of security risks, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and application-layer Distributed Denial of Service (DDoS) attacks, to name just a few ones.
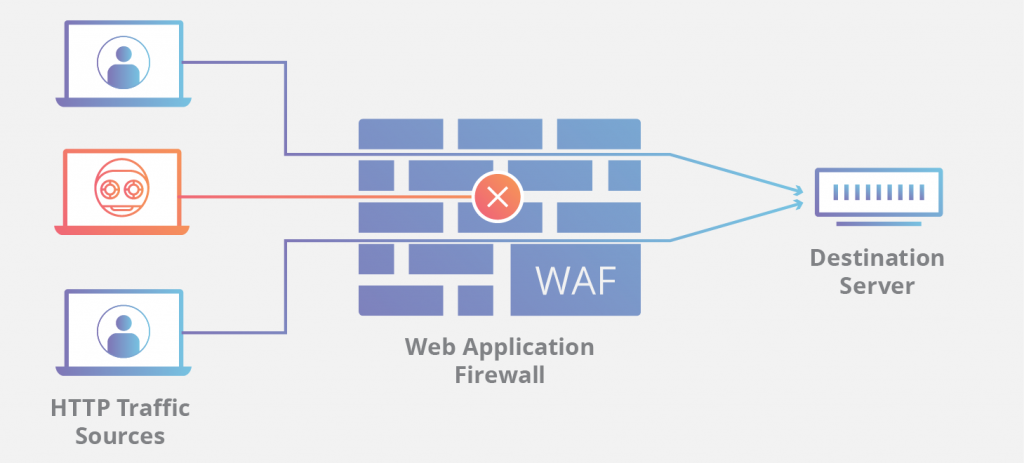
In summary, a Web Application Firewall acts as a gatekeeper for web applications, continuously monitoring, analyzing, and filtering traffic to protect against a wide range of online threats and vulnerabilities. Its ability to detect known and emerging threats, coupled with its customizable rule sets and logging capabilities, makes it a crucial component of web application security.
The WAF system relies on several operations such as Traffic Inspection (the requests enters the server and then WAF intercepts then inspects the request), Request Analysis (the WAF system will look for possible suspicious or malicious activities preventing threats) or Filtering the connections (if the request is considered malicious the WAF can take several actions including blocking,redirecting or challenging with the CAPTCHA to witness if the request is legitimate or malevolent)
The power of a WAF lies not only in its ability to recognize known attack patterns but also in its capacity to detect emerging threats through advanced heuristics and behavioral analysis. It operates based on rule-based policies, which can be customized to match the unique requirements of the protected web application or website. These policies determine how traffic should be handled, permitting legitimate users while blocking malicious activity.
A comprehensive logging and reporting system further enhances the WAF’s capabilities. It provides administrators with vital insights into the state of web traffic and security events, offering invaluable data for incident response, compliance reporting, and continuous improvement of security measures.
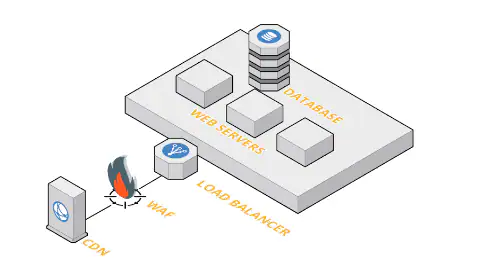
Whether deployed on-premises or in the cloud, a WAF is adaptable and scalable to accommodate the specific needs of web applications and the ever-evolving volume of web traffic. It can integrate seamlessly with other security tools and services, such as intrusion detection systems (IDS), intrusion prevention systems (IPS), and security information and event management (SIEM) platforms, to create a cohesive security strategy.
Such as A2F the WAF system has it’s own weaknesses going from False Positives and Negatives alarms( WAFs may generate false alarms (false positives) by blocking legitimate traffic, or they may fail to detect sophisticated threats) to the Overuse of Computer Ressources by the fact that WAF is greedy for IT resources while dealing with high trafic or DDOS attacks.
In a world where cyber threats are relentless and ever-evolving, the Web Application Firewall is an essential guardian of the digital realm. It ensures the protection of online assets, the preservation of sensitive data, and the unwavering availability and integrity of web applications in the face of the formidable challenges posed by today’s threat landscape.


0 commentaire